Page 6 - December_Newsletter_2023
P. 6
Are we ready to go now? Not really.
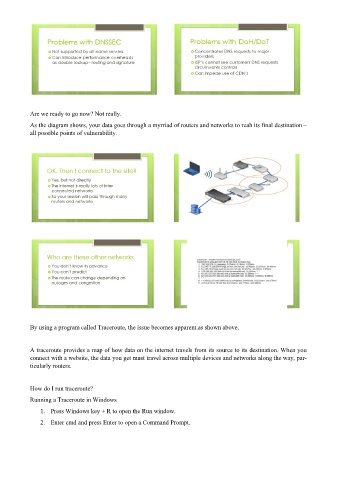
As the diagram shows, your data goes through a myrriad of routers and networks to reah its final destination –
all possible points of vulnerability.
By using a program called Traceroute, the issue becomes apparent.as shown above.
A traceroute provides a map of how data on the internet travels from its source to its destination. When you
connect with a website, the data you get must travel across multiple devices and networks along the way, par-
ticularly routers.
How do I run traceroute?
Running a Traceroute in Windows
1. Press Windows key + R to open the Run window.
2. Enter cmd and press Enter to open a Command Prompt.